by Pierluigi Paganini*
In this article, we discuss Single Sign-On, exploring what it is, its advantages and risks, the different ways it can be structured, and the systems that can be used to implement it.
What is Single Sign-On
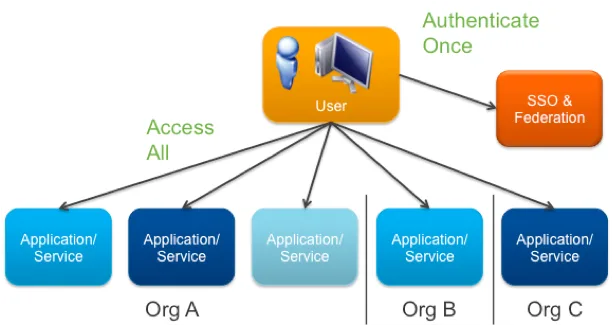
Single Sign-On, also known as SSO, is a system in which an access control mechanism allows an authorized user to authenticate once in order to access multiple applications, services, and resources.
In a Single Sign-On model, authentication requests are managed by a third-party system that has previously validated the user’s credentials. Whenever the user attempts to access a service to which they are authorized, their requests are forwarded to the central system that manages authentication. The user is therefore not required to re-enter their credentials.
The main driver behind the adoption of a Single Sign-On system is the need to simplify the authentication process. Users no longer have to handle secure access management themselves. This brings advantages in terms of security and maintainability for both users and system administrators.
Advantages of Single Sign-On
The advantages of a Single Sign-On system include:
- simplified password management. The more passwords users need to remember, the more likely they are to choose weak passwords or reuse the same password across multiple services, reducing security;
- simplified access to services;
- enhanced security and optimized management of security policies
- compliance with minimum security measures required by regulations on data security and management.
Risks of Single Sign-On
The risks of Single Sign-On, instead, relate to the third party managing user access.
Because of the very nature of Single Sign-On processes, the third-party entity authenticating user access to various services is the key component. The effectiveness and reliability of the entire system depend on the correct implementation of the authentication functionality.
For example, a third-party system that cannot manage the full user base simultaneously may cause service unavailability. A similar issue arises if, for any reason, the system stops functioning.
Differences between types of SSO
SSO systems can be implemented in different ways, depending on how user credential repositories are managed.
There are three main approaches to implementing an SSO system: centralized, federated, and cooperative.
Centralized SSO
In the centralized approach, a single, centralized database contains the entire user base. This approach is typically used in organizations where a central authority manages authentication requests for all employees.
Federated SSO
This approach is based on the federation of different identity providers. Whenever a user accesses systems managed by one provider, they are automatically authenticated for all services managed by the others.
This model is extremely useful in institutional contexts where different entities provide services to citizens. Each user can authenticate once through any provider and seamlessly access all services within the federation. For example, in a municipal administration, a citizen could authenticate through the civil registry service and then access tax-related services without having to authenticate again.
It should be noted that in such a model each federated provider maintains control over its own security policy.
Cooperative SSO
Cooperative Single Sign-On is based on the principle that each user depends on only one of the federated identity providers for each service.
As with the federated model, each provider independently manages its own security policy.
*Pierluigi Paganini
Member of Cyber G7 2017 Working Group at the Italian Ministry of Foreign Affairs
Member of ENISA Threat Landscape Stakeholder Group
SIPAF Contributor at the Italian Ministry of Economy and Finance








